This is a guide on how to setup a VPN kill switch with UFW, aka Uncomplicated Firewall. Sometimes a VPN service or OpenVPN drops the connection for whatever reason and displays your IP address. It might mean that you lose your connection to a stream which is geo-blocked in your country, or your Internet service provider (ISP) finds out you are doing something like illicit torrenting (which we do not condone here at htpcBeginner). They might throttle your Internet connection, or worse, you could end up with a fine. To avoid this, learn how to protect yourself with a VPN kill switch!
Table of Contents
Prerequisites and kill switch definition
Like the name implies, a VPN kill switch with UFW will terminate your connection for your personal IP address which is not encrypted. Before beginning, you'll need a few prerequisites:
- A Linux distribution such as OSMC or Ubuntu.
- A VPN provider like IPVanish
- OpenVPN [Read: How to configure VPN on OSMC with OpenVPN for Raspberry Pi]
Installing UFW VPN kill switch
Open up a terminal and type the following commands to update apt and install UFW:
sudo apt-get update sudo apt-get install ufw
We need to enable UFW to run this command:
sudo ufw enable
Surfshark VPN Exclusive Offer - 82% off ($2.39/month):
♦ Hide your browsing (no logs), Anonymize Streaming and Downloads
♦ Wireguard Protocol support for VPN.
♦ Circumvent Geo/Country Restrictions and access worldwide content
♦ Works on Windows, Mac, Linux, Android, iOS, Router, and more
♦ 1 TB Encrypted Storage
♦ Money back guarantee - Sign Up Now
Gather information about your IP addresses
Before we continue configuring UFW, you need to know your VPN providers' external IP address. To do that, run the following commands which go to the OpenVPN folder and display the .ovpn files.
cd /etc/openvpn ls
Here you have listed a bunch of .ovpn files. You have to choose the one you like, the fastest perhaps. Depending on how it's named, it could be something like au3.nordvpn.com.udp1194.ovpn or client.conf. [Read: Guide: Configure OpenVPN to autostart on systemd Linux]
To display the file information of .ovpn file run the command (where it says yourovpnfile.ovpn you need to type your chosen ovpn file name instead):
cat yourovpnfile.ovpn
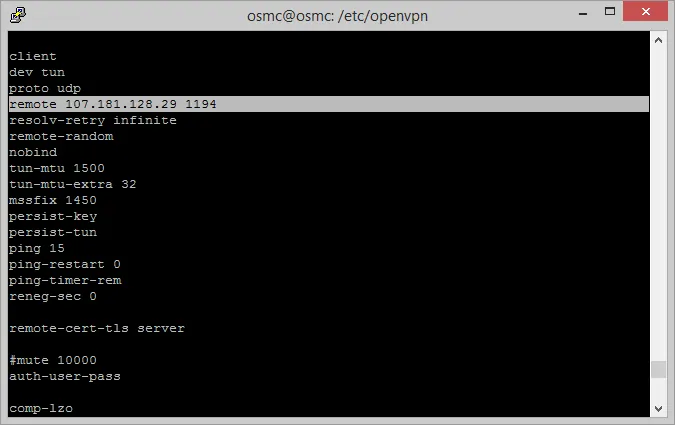
You should see something similar to this, on the highlighted line where it says remote, write those numbers down or a take screenshot of it. [Read: Guide: Configure OpenVPN autostart Linux connection]
The last piece of the puzzle which is your internal IP address. Run the command:
ifconfig
If your Linux box use wifi look for wlan0 if it uses an ethernet cable look for eth0.
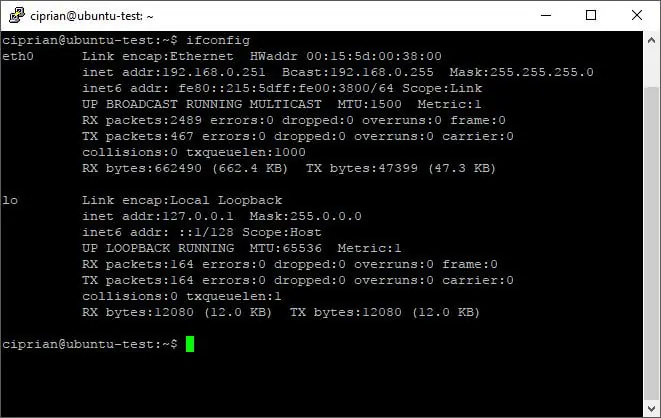
This address might differ from yours. In the example above, look for the line that says inet addr:192.168.x.xxx and write your address down, where it says Bcast:192.168.x.xxx.
Configure UFW VPN kill switch
Have a look at these UFW commands.
Now let's allow access on the LAN network so that SSH is possible on your home network. Run the command:
sudo ufw allow in to 192.168.X.0/24 sudo ufw allow out to 192.168.X.0/24
Notice that the X you need to fill in your internal IP address. This is a typical looking internal IP, but they can differ so please double check your ifconfig.
Run the following command to block all connections except LAN. Next we are going to make an exception for the VPN. I'm assuming you are using the tun0 for your VPN so it can connect to the outside world. Run the command.
sudo ufw default deny outgoing sudo ufw default deny incoming sudo ufw allow out on tun0 from any to any
Find your VPN IP address, the one you typed down and run the command below:
sudo ufw allow out to 107.181.128.29 port 1194 proto udp
In my case that is 107.187.128.29 on port 1194, and the port number is the one after the IP address. The proto or protocol is UDP in this case.
Optional: If you want your device to be connectable by others, you should run this command:
sudo ufw allow in on tun0 from any to any
Check if the rules work run the command:
sudo ufw status
Once that's finished, your VPN kill switch is complete. [Read: Install OpenVPN access server using Docker - Private VPN server]
Create a VPN kill switch with UFW: Final thoughts
You have a made a set of firewall rules that works as a VPN kill switch. All there is left to do is to test and enjoy it. Since you've figured ouw how to protect yourself with a VPN kill switch, try reading about a VPN and DNS to decide which is best for you.
What VPN tips do you suggest for staying secure while browsing?



![8 Amazing Raspberry Pi Ideas [2022]: Beginners and Enthusiasts Raspberry Pi ideas](https://www.smarthomebeginner.com/images/2021/09/raspberry-pi-4-dev-board.jpg)