It's 2023 and I see the world of technology constantly evolving around us. We are moving on from old technology and into the new, exciting future with cheap, renewable energy, powerful and efficient microchips, and even self-driving cars. But one thing that hasn't changed for thousands of years... PASSWORDS!
Now if only we could find a way to manage all of these irrational P4$$w0rDz!
Password managers are not a new concept, and have existed for years. They can be a great way to ensure we aren't falling into the typical trap of reusing short, memorable passwords based on our pet's name!
Be the ONE IN 200,000 that read this...This article costed over $250 in writing, editing, and publishing costs. If this helps you consider becoming a member or sponsoring our work. You will gain benefits such as discord roles, exclusive content, ad-free browsing, raffles, and more.
However, entrusting your most critical knowledge to a hosted service can lead to the services themselves being alluring targets. Thus we see the advent of self-hosted password managers. Let's take a look at some of my favorite self hosted web based password managers.
Table of Contents
- Background Information on Password Management
- Picking a Good Password Manager
- Best Self-Hosted Password Managers
- Advanced Self Hosted Password Manager Options
- Honorable Mentions
- Other Tested Password Management Solutions
- FAQ
- Can I host my own password manager?
- What is the difference between cloud and self-hosted password manager?
- What is the catch with password managers?
- I'm using a password manager, but how can I get my family to use it?
- What if the developer stops working on the application?
- How can I make sure I don't get locked out of my account or forget my master password?
- What about 2FA/MFA for Password Manangers?
- Conclusion
Background Information on Password Management
Without getting into any sort of detail about the history and reasons we still use passwords, we can all agree that they are frustrating.
In recent years, bad actors have gotten better and better at cracking passwords, breaching databases, and sly phishing schemes. This applies to small and large companies alike. And 2023 is on pace to be the worst year yet.
These breaches have led to all sorts of counter-measures: Impractical password requirements, short expiry dates, multi-factor authentication (MFA), OAUTH, OIDC, etc. Some of these steps are more effective than others, but don't really mitigate the main issue: people aren't good at creating and remembering strong passwords.
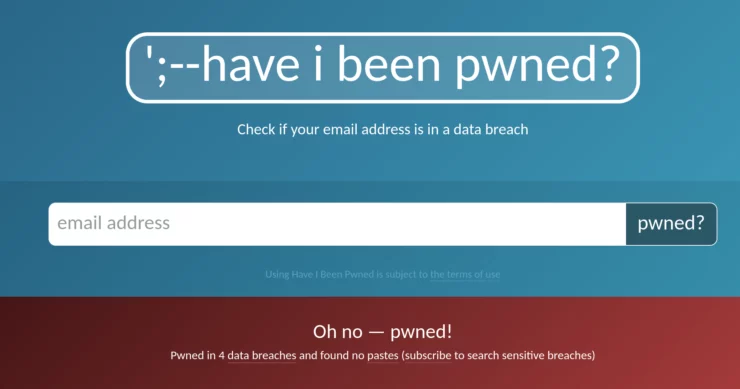
Have I Been Pwned?
Services exist that can help to identify if our accounts have been compromised. If you haven't checked out haveibeenpwned.com before, I highly recommend you do, and change any passwords that could have been in any compromised services.
Alternatives to Passwords
There are a number of improved (non-password) methods coming into popularity like facial-recognition, fingerprint-scanners, and hardware keys. But most websites aren't nearly advanced enough, and thus we are stuck with passwords.
Two Factor (2FA) and Multi Factor (MFA) authentication protocols have been in use heavily lately, and at least provide a small amount of protection. These protocols require you to click a link, enter a multi digit code, or provide a second form of authentication that only YOU would have access to. They do help mitigate some attacks, but if you've reused the same password for your bank and your email account, you haven't provided a difficult task for a hacker.
Password Management Mistakes
Password managers are not magic. If you are reusing the same password across multiple services, the password manager will not help to stop these types of attacks. The same goes for storing your One-Time-Passwords (OTP) in your password managers - if someone is able to access your vault, you no longer have multiple authentication factors!

However, understanding why we might want a password manager (and how to use it properly) will significantly increase your online safety and reduce the chances of accounts getting hacked - EVEN if you end up falling for a phishing scam.
Picking a Good Password Manager
Everyone will have their own specific set of requirements for a password manager (like any piece of software really). However, I think there are some major points to look for, and a few minor points to consider as well. The following is my list of factors I consider when looking at a password manager:
Critical
- Secure and transparent - One of the easiest ways to prove security is with a "Third-party Audit". This means that a person or group outside of the developers does a review of the application's code as well as testing it for weaknesses and flaws (often referred to as "pentesting" or penetration testing). This third party is preferably a reputable security researcher.
- Well maintained - Some applications can go for months or even a couple of years without any updates. To me, something as mission-critical as a password manager should be updated regularly.
- Mobile app (friendly) - Mobile phones are so prevalent that the experience should be seamless whether you are on your phone or computer.
- Password generator - Why go through all of the trouble to have a password manager if it can't even generate strong passwords for you? Preferably it should have the ability to adjust length, strength, and restrict certain symbols for the websites that don't like @$~#_ etc.
- Ease-of-use - Usability is key when adding a new application to my growing stack. This is triply important if it's something I want my significant other or family members to buy into as well. This also discourages sending passwords over SMS, email, or a messenger.
Secondary
- Containerized
- Transportable - If I decide to change services, I better be able to migrate hassle-free.
- Multi-User support - and sharing between users
- Auto-fill / browser integration
- Password data breach checking
So, with these requirements in mind, let's take some of the best self-hosted password managers.
Best Self-Hosted Password Managers
Below I give a list of my favorite password managers (in no particular order). I will give a brief introduction to the application itself and a quick summary of how it stacks up to my above requirements.
Next, these aren't intended to be in-depth installation guides or full reviews, just my thoughts and feelings on using the applications themselves, and finish with a summary Pro's/Con's section and some closing thoughts.
I prefer running my containers with rootless Podman, which could impact some of the installation and running, but I will try to keep things runtime agnostic. I am running everything behind a Traefik reverse proxy with self-signed TLS certificates for testing.
1. Bitwarden
We're starting off with the most well-known and likely most widely-used self-hosted password manager. As far as I know, the majority of people using Bitwarden are actually running Vaultwarden (discussed below). But before getting there, I wanted to take a peek at the root of it by reviewing the "parent" of Vaultwarden.
Personally, I am a huge fan of Bitwarden's business model - open source with affordable subscriptions that include tons of great features for individuals and businesses alike. They show a good amount of transparency and don't appear to hamstring the self-hosted version too much. Of course, their business model relies on people subscribing to get more advanced features, and if you can afford it, I definitely recommend supporting open-source projects!
For the review, Bitwarden meets all of my critical and secondary requirements. Off to a good start then! Most importantly, they are frequently audited and transparent about the results.
There are indeed both iOS and Android apps, as well as browser integrations for all of the most popular web browsers.
Sounds great, right?! Well... what about actually running this self-hosted open-source password manager.
Running and using Bitwarden
Getting Bitwarden up and running was a bit of a pain. The recommended method (and hardware requirements) are bordering insane for a self-hosted password manager.
Fortunately, announced in December 2022, Bitwarden now has a single "unified" container that lets you run a small, efficient instance in a more familiar fashion. Frankly, I tried the 11-container method and never got it fully working. I admit that it was mostly my fault - traversing the logs and problems across 11 containers was an enormous undertaking.
However, the unified approach was simple, and setup with a handful of environmental variables like we are used to. Starting the container and getting through the initial account creation was relatively painless.
If you want to try out the software, you will need to use a domain name and a TLS certificate. This made it more difficult for me to "just spin up a container" for a test environment to write this article. There are ways around it, but that's outside the scope of this article.
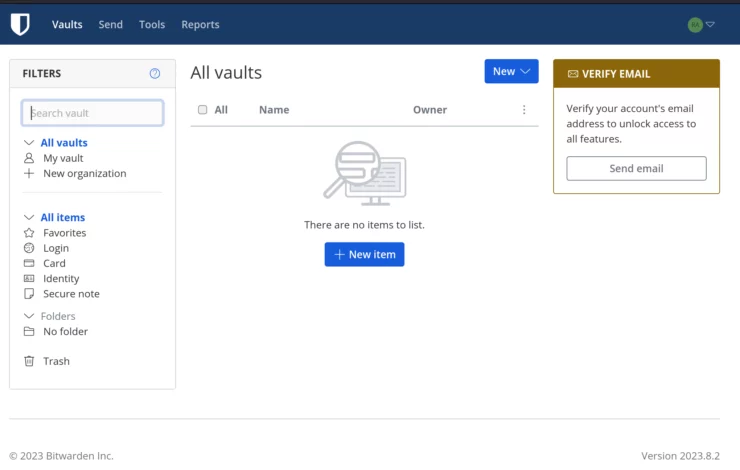
The application is pretty simple. Personally, I really like the simplified organization of different items and tools.
Creating a username and password for a new service is easy:
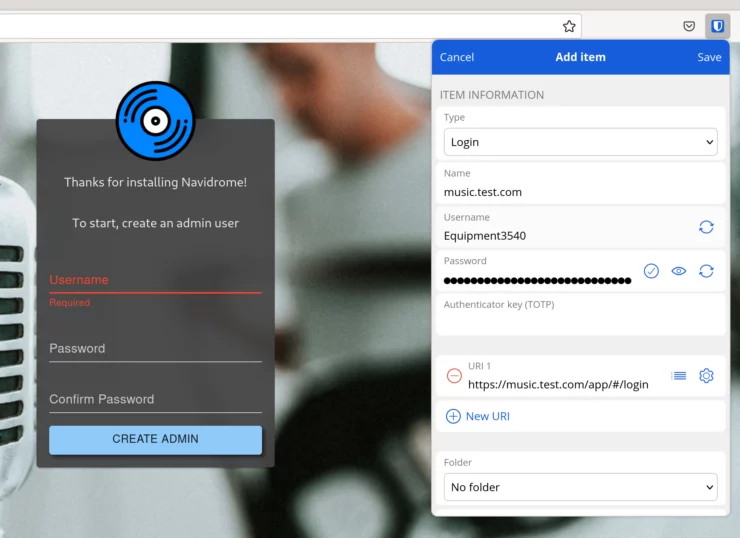
And to insert it (without having to copy-paste) is as simple as a keyboard shortcut, or clicking on an entry!
The android app is also just as intuitive, and can be secured behind a pin code or fingerprint scan.
Pro's/Con's
| Pros | Cons |
|---|---|
|
|
Final Thoughts on Bitwarden Password Manager
Bitwarden is a fantastic piece of software with options for self-hosters. I feel as though they have spent their effort in the right places, and understand the critical points of what make a good password manager. I have very little to complain about now that their unified container is coming into its own. Not long ago this wasn't an option and turned-off most self-hosters.
2. Vaultwarden
Although the Vaultwarden password manager project has no association with Bitwarden, it is similar and compatible with Bitwarden clients. In fact, I believe that the success of Vaultwarden is what has pushed Bitwarden to focus on its "unified" container approach.
Vaultwarden's popularity can easily be seen by the sheer number of stars and forks on the project's GitHub repository. Vaultwarden has leveraged Bitwarden's open-source password manager model to create an API-compatible server written in the Rust language. For the lay person, that simply means that Vaultwarden follows the same design laid out by Bitwarden, and allows the Vaultwarden server to work with any Bitwarden clients - including browser extensions, mobile applications, etc.
Some notable features for Vaultwarden are features of Bitwarden that are hidden behind the paywall. These include:
- Unlimited "Organizations"
- Sending files with "Send"
- MFA, including YubiKeys and Duo
- Emergency Access
Otherwise, the software is almost 1:1 comparable to Bitwarden. To me, there is only one glaring issue (albeit a relatively small one) is the lack of a proper third-party audit. Since we had no real alternatives previously (besides running 11 heavy containers), most people overlooked this fact. Now with Bitwarden's "unified" container on the rise, we must consider the importance of the security aspect. In fact, Vaultwarden is completely reliant on Bitwarden and its clients.
Running and using Vaultwarden
In stark contrast to Bitwarden, this really couldn't be simpler. [Read: Vaultwarden Docker Compose + Detailed Configuration Guide]
The project's wiki is honestly a fantastic resource with lots of information about all the nuances possible for running the app. It even includes rootless Podman instructions 😀.
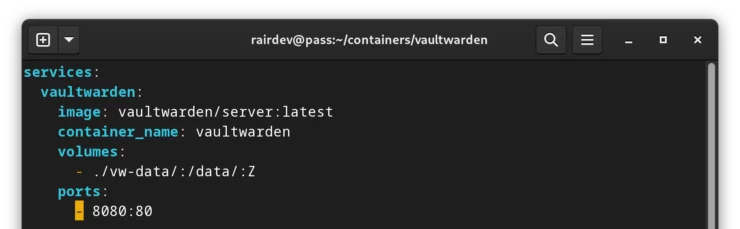
Once up and running, we repeat the exact same steps as above. The only (tiny) differences we will notice are the logo and the server info at the bottom of the page.
The vault even looks familiar, with the exception of seeing the "premium" banner printed over specific functions of the app.
For more on using Vaultwarden, literally just scroll up. The same things apply to what I wrote above for Bitwarden. They function identically, and even use the same Bitwarden clients. The only difference is the back end, which, once connected, is completely invisible to the user.
Pro's/Con's
| Pros | Cons |
|---|---|
|
|
Final Thoughts: Bitwarden vs VaultWarden
Vaultwarden's success in the self-hosted space has been primarily due to the difficulty of running Bitwarden. Most people have let slide the lack of a third-party audit since it had been really the only feasible way to run Bitwarden. And an easy solution to this problem exists: Make the application only accessible on your home network or via a VPN like Wireguard.
Personally, I love Vaultwarden and have been using it for a couple of years now without issue. The interface is intuitive, easy to manage, and both my wife and I are heavy users. But I must admit I am now torn between staying with Vaultwarden or moving to Bitwarden's unified container.
In my opinion, Bitwarden and Vaultwarden are the best open-source self-hosted password managers.
Be the ONE IN 200,000 that read this...This article costed over $250 in writing, editing, and publishing costs. If this helps you consider becoming a member or sponsoring our work. You will gain benefits such as discord roles, exclusive content, ad-free browsing, raffles, and more.
3. Passbolt
Frankly, I had never heard of Passbolt until I started rummaging around the internet trying to see what was out there and what people were using for password managers. I stumbled upon Passbolt and was immediately impressed. It ticks nearly every box in my Critical requirements, including transparency about security.
I was also impressed with their recent blog post detailing the beginnings of the company and the application. Notably, the company started using KeePass, which is in my honorable mentions list below.
Beyond that, nearly every single other requirement is met. The free Community Edition of the Passbolt password manager even allows for unlimited users, groups, and passwords. This has got me very interested!
Running and using Passbolt
The good news here is that running Passbolt is relatively straight forward. It is encouraged to run in a container (woohoo!) and even includes a rootless image! It requires a database (mariadb/mysql or postgresql) and the Passbolt container itself. Unfortunately, no SQLite support to slim down the requirements even more, but I can't complain too much.
Like the above two applications, Passbolt does require a TLS certificate to work. In this example, I was able to get it working (for the most part) with a self-signed certificate for testing, but ran into some issues later. Using a valid certificate is required and would have eliminated my issues.
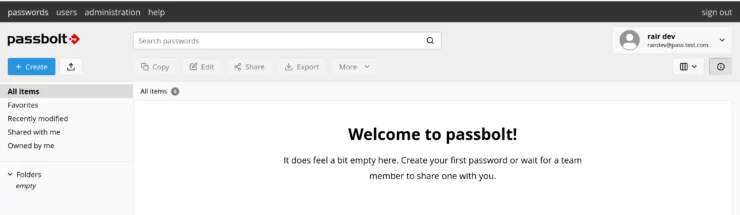
I like the interface - unobtrusive, clear, and doesn't try too hard to impress with superfluous animations and flare. It IS a password manager after all...
Using the extension was a breeze, and in many ways similar to the Bitwarden client. Once you've signed into the extension, it overlays onto existing sign-in pages. This allows you to auto-fill the form in 2 clicks, or create new credentials on the fly. I really appreciate the ease of use of the extension.
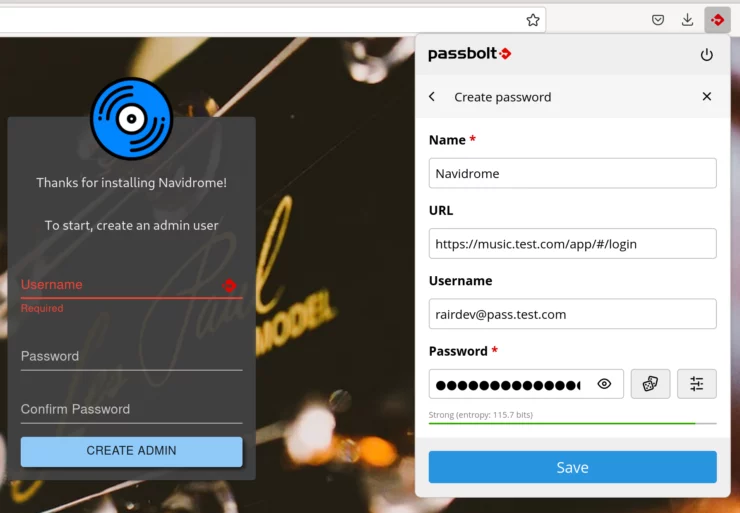
Truth be told, I have no complaints on the use of the application itself in its various forms. They are simple, intuitive, and well-thought.
I couldn't get the mobile app to work in my lab environment, so I recommend checking it out before fully committing to Passbolt as your password manager.
Pro's/Con's
| Pros | Cons |
|---|---|
|
|
Final Thoughts on Passbolt
For never having heard of Passbolt password manager, I must say I am truly impressed. I really appreciate the ease of setup, the user interfaces, and the features available in the free Community Edition. At the end of the Con's section above, I added a few things that are not "yet" available, but they do in fact appear on their roadmap.
I was definitely frustrated by the hard requirements of the browser extension, and the complication of setting up the mobile app. But again, I think those boil down to the fact that I'm trying to test everything out in a lab environment. Passbolt definitely fits into a nice niche where Bitwarden and Vaultwarden are lacking.
4. Psono
Psono is a password manager that I stumbled upon, but initially wrote off. After reviewing some of the other applications on my list, I decided to come back and give it a shot. My initial concerns still exist (more on that in a bit), but overall, I was happy I tried it out. It is created by the esaqa GmbH company in Germany, but appears to only have one contributor (the CEO).
Psono bills itself as an open-source self-hosted password manager for teams. This piqued my interest as I am looking for a solution that includes support for multiple users and sharing passwords between them.
Surprisingly, I found that Psono ticks nearly every box for me. I didn't initially find any evidence of a third-part audit, but digging around the blog, found an audit by an Italian security firm in Jan. 2022. They have also done a self-audit (in March of 2018).
It appears that they are using some good cryptography libraries, similar to those used for Wireguard. But their security model is heavily based upon self-approval, automated testing, and GitHub vulnerability scans. This is all and well, but doesn't guarantee bad code especially considering it's a one-man show. Minor concerns aside, let's see what's offered.
Running and using Psono
Psono offers, for free, both a Community Edition (CE) and a limited Enterprise Edition (EE). It appears that the CE gives you pretty much everything you could imagine, with the only benefit of moving the to EE would be for SSO. The one downside to the free EE is you are limited to 10 users. Not bad if you ask me! The following review is of the CE.
Installing Psono is fairly straight forward - the documentation is refreshingly thorough and easy-to-follow. I was able to quickly get things up and running with a simple compose file.
I had 0 issues running everything in rootless Podman.
The admin panel has some nice graphs and the main dashboard is clean, albeit a bit confusing at first.
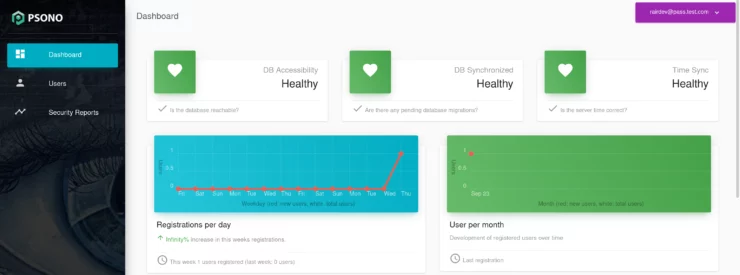
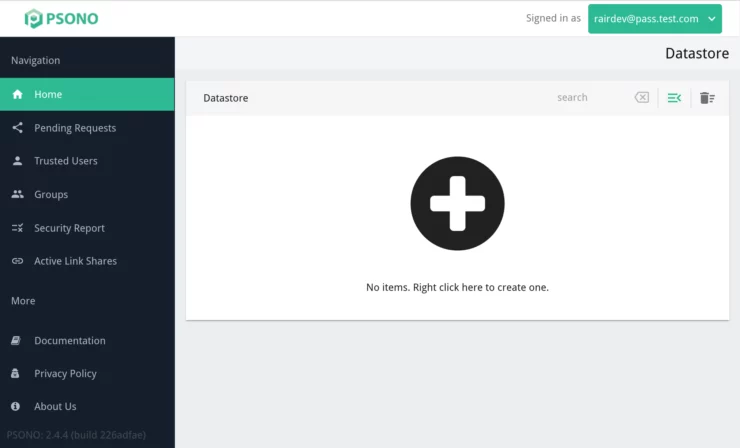
I really like the layout of the application. Some of the functions are not as obvious as in other apps, but after a few minutes of poking around I was able to find lots of cool features. There is a User Manual, although it was not obvious to find at first glance.
Creating new passwords, groups, and sharing them is easy. I also really like the "link share" option, which is akin to Bitwarden's "Send" feature.
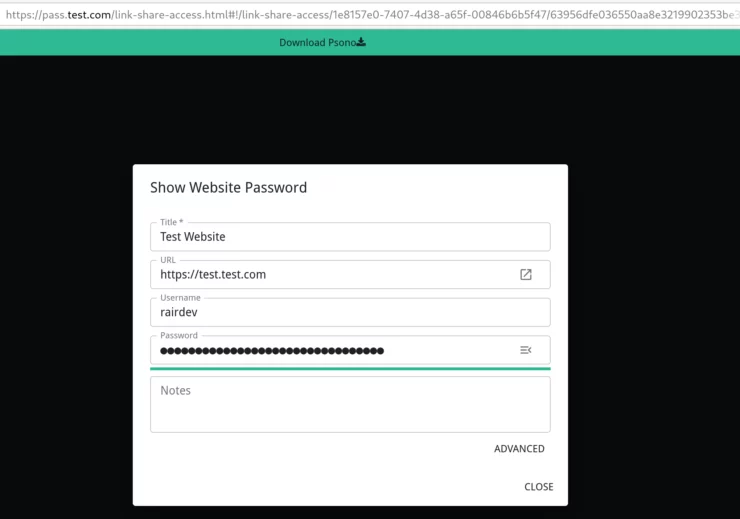
The only thing I found a bit confusing was creating new entries from the browser extension. You must type in a username yourself before using the "Generate Password" option (or the username will be saved as a blank within Psono).
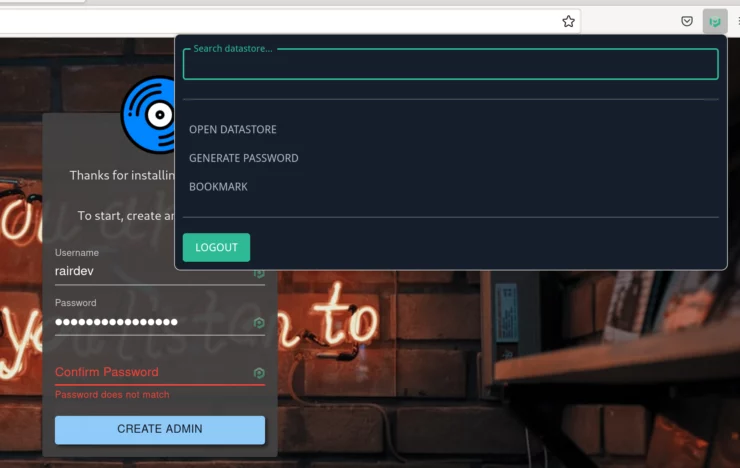
Also, using Generate Password only fills in the password field once, and to get it again for the "Confirm Password" section, you'll have to go find it, copy it to your clipboard, and paste it in manually.
The Android app also appears to be quite good and integrates into the OS with auto-fill. Unfortunately, I once again could not get a chance to test it out properly since the emulator was unhappy about my self-signed certificates.
Pro's/Con's
| Pros | Cons |
|---|---|
|
|
Final Thoughts on Psono
Honestly, I was blown away by Psono. Truly, it is a well-developed application and even more impressive that it is done by a single developer. That said, I think there are some shortcomings with regards to overall usability and security. It is true that Psono is using a relatively modern and stable technology stack, but I think I would still lean towards running the application behind a VPN until I see more transparency and verification of security.
Features wise, Psono appears to offer the most in its free versions. It was the only one I found with SSO support available in a free flavor of the application. I am indeed glad I did not pass up reviewing this gem.
Advanced Self Hosted Password Manager Options
OK n00b, but what about something to REALLY impress my friends?
- signed: the internet
Perhaps the target audience of the blog doesn't really fit into this section, but I wanted to throw out an interesting pick that is awesome in its own right. However, this will require a bit more knowledge and comfort with the command line.
5. gopass
Similar to pass in the Honorable Mentions section below (and in fact inspired by the project), gopass shares almost entirely the same feature set as pass. However, it is designed with team features at its heart - which is why gopass is here and pass is below.
Overview of gopass Self-Hosted Open-Source Password Manager
The basis of this application is to simply create GPG encrypted password files stored locally or in a Git repository (the default). In general, you interact with gopass via their command line tool to add, manipulate, etc. your passwords. The Git repository will also track your password history and allow a "sync" across devices. This is where we get into the advanced side of things. The Git repository can be easily self-hosted, which is why this ended up on our list.
Beyond the features of pass, I wanted to highlight a few additional features that gopass brings to the table.
- Hooks (run a script after an event: like telling clients to sync on a password modification)
- haveibeenpwned integration
- JSON API - for use with browser extensions
- Multiple store support (example: To use a separate Git repo for you and your family, and a separate one for work)
Running and using gopass
Since this is a relatively advanced setup, I will stop here for now. If there is enough interest in this setup, I will create a detailed guide with examples for how to use it with multiple users.
So, let us know in the comments section if you are interested in know more about gopass.
A huge bonus is that besides the basic CLI version of the app, there are also browser extensions, and compatible mobile applications among other compatible integrations.
Pro's/Con's
| Pros | Cons |
|---|---|
|
|
Final Thoughts on gopass
Gopass is a nice evolution of the original pass and aims to take the best parts of pass and builds upon them. This implementation feels like it is going in a good direction. I will caution however, that open-ended projects like this one don't put a lot of limitations or structure around users' actions.
The point of using a Git repo does help to minimize these types of issues, but will not eliminate them. This makes this recommendation both advanced is setup and use.
Honorable Mentions
The following applications were promising in many ways, but missed something key in my opinion. That doesn't mean write them off. But you should be aware of their limitations - which exist at the time of writing, and may change over time!
6. pass
You may recognize the creator of pass. Indeed, it is Jason A. Donenfeld - the creator of my favorite VPN protocol, Wireguard. Not that I recommend "riding on the coattails" of other successes, but we can be reasonably sure that security is at the heart of this project. Otherwise, the application ticks all of the major requirements and most of the secondary ones as well.
Like above, this app creates GPG encrypted files stored locally. In its most basic form, you can use the pass command line tool to access your passwords. In a more advanced form, the passwords live in a Git repository similar to the above gopass.
Final Thoughts on pass
Personally, I find this to be an awesome option. The only hangup for me is that to use this with a significant other, who is moderately technologically literate, would quickly become a point of frustration unless many tasks are automated.
Yes, some of this could work via webhooks, etc. But if I wanted to add, for example a family member, it takes a lot more effort than just signing up with an email address.
7. Padloc
Padloc is a very nice-looking password manager that tries to bill itself as THE easiest self-hosted password manager available. While I appreciate the sentiment, the reality is a bit different.
I highly appreciate the fact they've been third-party audited and are transparent about their security.
Setting up Padlock is a bit odd in that both the server backend AND the web app needed separate TLS-protected (https) domains to be able to communicate even on the same host. I understand the principle of Zero Trust Architecture, but from a self-hosted approach, this doesn't seem to actually prevent any potential attacks.
I like the way the app looks and feels. But the main breaking point for me was when I went to install the Firefox extension.
After installing, I realized there was nowhere to put in my self-hosted server name. That's because their servers are hard-coded into the extension for "security reasons".
Thus, the only way to use your own server is to build each extension (and mobile app!) yourself. True, it's a single command line each, but if I am to use this application with anyone else, that means I'm in charge of building and distributing extensions and apps each time there's an update available. No, thank you.
Final Thoughts on Padloc
The idea is there. But the developer often replies to issues with "sorry we're a small team with other priorities". I understand this, but it won't win you more users. Seeing how much easier other password managers are to setup and use, they are shooting themselves in the proverbial foot.
8. Passky
Passky is a very nice idea. I like the work that has been put in, and most of my critical and secondary points were met. But, in my mind, a few questions exist. Security (well encryption) is mentioned, but no talk of audits.
The developer does discuss the idea of a third-party audit, and mentions that most of the libraries that have been used are well-tested. However, the current list of issues has too many security or privacy related requests created by members of the parent company.
The application is fine, but definitely basic. Multi-user support exists, but there's no way to share anything between users or create groups. The password generator is OK, and has some basic configuration available.
Also, I couldn't find a way to change my master password or my email address after account creation. To me, these are some basic features that are either missing or undocumented.
Final Thoughts on Passky
I like the idea of Passky. However, I had too many pesky issues that made the use of the app frustrating. It appears that the developer is active, and with future updates, could be a winner due the lightweight nature, security/privacy-first approach, and effective design.
9. Passit
Passit is very basic password manager that applies a simple but sane security model. My main concerns here are that the developer relies on the "well it's open source so you can audit it" method to ensure pentesting and threats are mitigated 🤔.
There also appear to be very infrequent updates - this isn't always a bad thing, but the app feels a bit primitive in its current state and the handful of issues make it difficult to recommend over other apps.
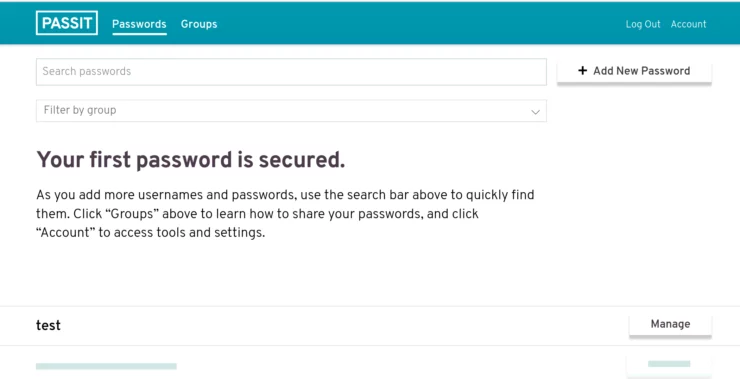
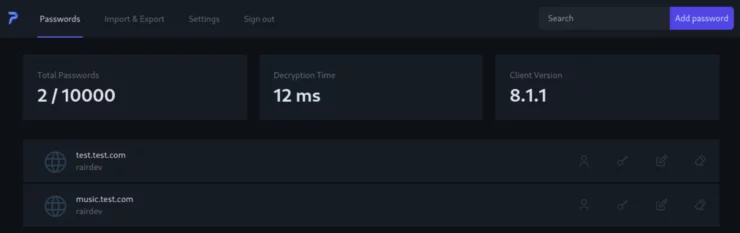
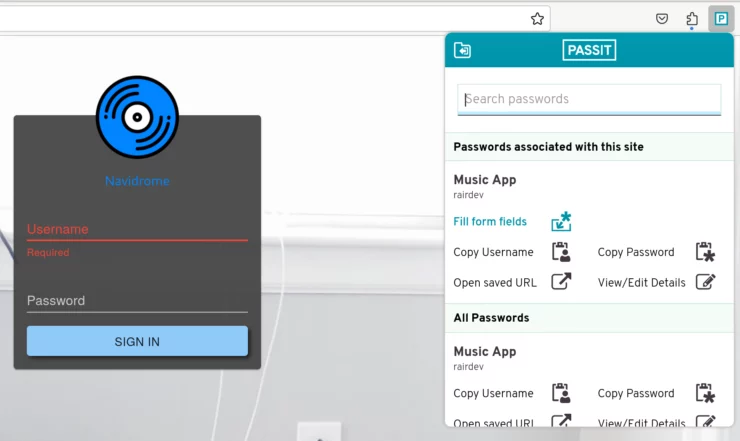
The user interface is basic, but works. I appreciate the ability to use groups and share with other users. There is a password generator, but no apparent way to configure the password length or character selection. I also could not find a way to create an entry from the browser extension - it appears to be a read-only version of the database.
Final Thoughts on Passit
Does Passit work? Yes. Does it have any frills or features? Eh... no not really. It's not necessarily a bad application, but doesn't offer anything outstanding. The lack of updates and third-party security audit do concern me a bit, but that depends on how you plan to use your password manager.
Other Tested Password Management Solutions
For transparency's sake, I also tested the following.
10. PassWall
PassWall is a good-looking concept, but there haven't been any updates in over a year (at the time of writing). The browser extension and mobile apps still appear to be a work-in-progress as well. Keep an eye out for updates as it looks modern and well-designed.
11. sysPass
sysPass is also a very promising application with loads of options and an extensive API. However, the server has not updated since July 2022. There are also no apparent third-party audits, browser extensions, or mobile applications.
12. KeePassXC / KeeWeb
KeePassXC was my first password manager and still holds a special place in my heart - it is truly awesome. However, it doesn't fit in the self-hosted space. You can sync your database across devices if you're using a services like Syncthing or Nextcloud, but it doesn't always work seamlessly. There is a web-hostable version of the app with KeeWeb but hasn't seen updates for a while, and is looking for a new maintainer.
FAQ
Can I host my own password manager?
Of course, you can self-host password manager (e.g. Bitwarden, Vaultwarden, and more). In fact, the majority of the password managers listed here are open-source and self-hoted.
What is the difference between cloud and self-hosted password manager?
With a cloud-based password manager, you are trusting your credentials in a third-party cloud environment. They can be very reliable but also have bigger targets from hackers on their back (e.g. LastPass). With a self-hosted password manager, you are storing everything in your environment. While a smaller target, with improper security, you could compromise yourself.
What is the catch with password managers?
The only catch with password managers is you are trusting your most important data with someone else. A cloud-hosted password manager can be hacked or a self-hosted password manager can have bad code that could "call home" or have vulnerabilities.
I'm using a password manager, but how can I get my family to use it?
The applications listed here are EASY! Sit down, help them set up the apps on their devices, and teach them how easy they are to use. Honestly, I think it's faster for me to login with my password manager app than typing in even a short, memorable password.
What if the developer stops working on the application?
One important factor I always point to when choosing applications in the self-hosted space is their transportability. Can you easily move your data from one service to another? Look for password managers with both import and export functionality.
How can I make sure I don't get locked out of my account or forget my master password?
Some password managers offer emergency access, emergency access kits, or a set of codes that can be used once to unlock your vault. I recommend printing or writing them down, and locking them away somewhere safe. As for backing up your password manager's database itself, always follow the 3-2-1 backup scheme!
What about 2FA/MFA for Password Manangers?
Two-factor Authentication / Multi-Factor Authentication are both excellent ways to further strengthen your security online. Unfortunately, many applications still rely on SMS based codes which can be stolen with SIM-spoofing - not common or easy, but it has happened.
One-time-passwords (OTP), like authenticator apps, are a good way to secure your accounts as well. But keep in mind that if you have both your password manager AND your authenticator app on your phone, and your phone is stolen and unlocked, you've given away the only security you had.
Finally, perhaps one of the best MFA options is hardware keys like YubiKeys. They are little USB (or otherwise) sticks that you must treat like the keys to your car or house. They aren't in use everywhere, but more and more services are adding support for them regularly.
Conclusion
Password managers are effectively uncomplicated pieces of software (essentially databases with security at heart), but they are becoming a necessity to stay safe across the internet. While there are many hosted options available like 1password, ProtonPass, Google Password Manager, etc., remember that not long ago LastPass was hacked - and not for using weak cryptography or bad code!
The danger then, is, the large target that these services have become. If you are self-hosting applications, a password manager should be one of your first choices. There are multiple available that are easy enough for anyone to use, leaving no excuse as to why you AREN'T using one! One successful phishing attempt could lead to a massive leak of personal data.
Having said that, setting up your own self-hosted password manager "properly" is even more important or you face the same list. So, stay tuned for more articles on setting up some of the above-mentioned password management software, the right way.
I've been using a password manager for many years now, and sharing it with my significant other. Like many of the applications featured on this site, we can't imagine NOT using a password manager to keep our family a bit more secure.








![5 Best NAS with SSD Cache for Home and Office [2023] A feature image that shows all 5 of the best NAS that supports SSD caching for home and office](https://www.smarthomebeginner.com/images/2023/10/best-nas-with-ssd-cache-feature-image.png)