Wireguard VPN as a protocol is a bit different than a traditional VPN. If you are new to it, I strongly suggest reading my Wireguard introduction for beginners.
In my Wireguard setup articles, I use the "server" and "client" terminology to simplify our understanding and make the transition to this idea a bit more comprehensible. The truth is, that Wireguard as a protocol simply creates secure "tunnels" between peer devices. How we interact with these tunnels, and how those tunnels connect is what gives Wireguard its flexibility.
Previously, I described Wireguard Mac OS client setup. In this post, let us look at how to setup Wireguard client on Android and configure it.
Table of Contents
- Wireguard Android Client Setup
- FAQs
- Why can't I connect to another device?
- Can I have more than one Wireguard tunnel active at a time?
- How do I add better security with a Preshared Key?
- Can I use Wireguard for Android with IPv6?
- How do I export my config if I generated it myself?
- Why can't I connect to the Internet after starting my Wireguard tunnel?
- How do I Include/Exclude an app from using the Wireguard tunnel?
- How can I automatically disconnect the tunnel when I am home, and automatically connect when I leave?
- Concluding Thoughts
Wireguard Android Client Setup
You will sometimes hear about a "Road Warrior" setup with regards to Wireguard. This approach embraces the traditional server/client model - no matter where we go, our device is always able to connect to a static "home" server. This article will follow this approach and give a basic walk-through on connecting our Wireguard Android "client" to a Wireguard "server".
Other Posts in the Wireguard Series:
- Wireguard VPN Intro in 15 min: Amazing new VPN Protocol
- Complete Wireguard Setup in 20 min – Better Linux VPN Server
- Wireguard Windows Setup: Powerful VPN for Windows
- Wireguard Mac OS Client Setup – The sleek new VPN
- Wireguard Android Client Setup – Simple and Secure VPN
- Ultimate WireGuard Docker Compose: with CF and Traefik Support
1. Install Wireguard Android App
Following the directions listed on the Wireguard website, download and install the Android Wireguard app via the Google Play Store or F-Droid App.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 2 Wireguard F-Droid App](https://www.smarthomebeginner.com/images/2021/09/0-wireguard-f-droid-300x614.png)
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 3 Wireguard Google Play Store](https://www.smarthomebeginner.com/images/2021/09/0-wireguard-google-play-300x618.png)
Launch the newly installed app, and we are greeted by an empty Wireguard window.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 4 Empty Wireguard App](https://www.smarthomebeginner.com/images/2021/09/1-wireguard-android-empty-300x623.png)
2. Create the Local Wireguard Adapter
Wireguard works by creating a virtual adapter to route your traffic through. There are 2 ways to connect your Android device as a client to a Wireguard server. Both require a set of configurations which can either be delivered to you as a single file/QR Code, or created through the Wireguard Android App itself. Let's look at both ways.
Option 1a: Importing a Given Configuration via QR Code
What is a QR Code?
QR Codes are a simple way to visually represent data. They are designed in such a way that cameras (along with basic software) can easily decode the data into something we recognize. This is often used to encode URL's. For example: the website address of a menu at a restaurant might be QR encoded so you can just take a photo and get the URL to avoid typing in a long website address by hand.
Generate the QR Code
In our case, the Wireguard config file is simply a bunch of text in a small file. If we want to import the config to our Android phones from say a Linux server (or computer), we just need to install a QR encoding software and pass the config into it. For example, on an Ubuntu machine we would need to:
$ sudo apt install qrencode $ qrencode -t ansiutf8 -r "peer.conf"
- Replace
peer.confwith the name of your config file
This will output a large QR code in your terminal. Leave it open while we import it from the Android device.
Scan the QR code into the Android Wireguard App
Now onto the Android device. As instructed, click the big blue (+) button in the bottom corner of the screen. Select "Scan from QR Code":
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 5 Select Scan Qr Code](https://www.smarthomebeginner.com/images/2021/09/2-wireguard-android-scan-qr-code-300x636.png)
If you haven't yet given the Android Wireguard App permission to use the camera, you might get a security pop-up. When in doubt, select "Only this time":
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 6 Android Camera Permission Warning](https://www.smarthomebeginner.com/images/2021/09/2-wireguard-camera-permission-300x368.png)
Your camera should now start. Point it at the QR Code. Make sure that the whole code fits inside the light-colored square on your screen.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 7 Scanning The Qr Code](https://www.smarthomebeginner.com/images/2021/09/2-wireguard-android-qr-code-300x372.png)
Lastly, you are asked to give the newly created tunnel its name. I wasn't feeling very creative and simply called mine "homeserver":
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 8 Name Your Wireguard Tunnel](https://www.smarthomebeginner.com/images/2021/09/3-wireguard-android-name-tun-300x599.png)
Click "Create tunnel" when you are finished and move ahead to activating the tunnel.
Option 1b: Importing a Given Configuration via File
Begin by transferring the config file(s) to your Android device.
Now onto the Android device. As instructed, click the big blue (+) button in the bottom corner of the screen. Select "Import From File or Archive":
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 9 Import From File Or Archive Option](https://www.smarthomebeginner.com/images/2021/09/4-wireguard-android-import-from-file-300x636.png)
We are greeted with a screen in which we must choose the config file. Navigate to the location where it is stored, and open the file.
The app will automatically generate the name from the config file. So, if your config file name is wg0.conf, the tunnel will simply be named "wg0".
Edit the Interface (Optional)
At this point you can click the toggle to the right of the tunnel name to get started. But before we do, let's click on the name of the tunnel itself to see the details of the adapter. We are now shown a more verbose overview of the tunnel including the configuration settings we imported.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 10 Click The Tun Name To Show Details](https://www.smarthomebeginner.com/images/2021/09/5-wireguard-android-edit-tun-300x423.png)
Here we can edit any details including the name if you would like something different than "homeserver". Click the "pencil" icon in the top right corner to begin editing the tunnel.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 11 Modify Settings As You Like](https://www.smarthomebeginner.com/images/2021/09/5-wireguard-android-edit-tun2-300x617.png)
When finished, simply click the 'Save' icon in the upper right corner. Continue to activating the tunnel.
Option 2: Create a Configuration of Your Own
In this scenario, we will create the configuration ourselves, and only pass the "Public Key" to the server to add it as a new [Peer]. You will need, however, a few details from the Wireguard server you intend to connect to: Public Key, Endpoint IP Address and Port, Allowed IP(s).
Create a new tunnel
At the bottom of the Android Wireguard app screen, click the plus sign (+) and select 'Create from Scratch':
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 12 Create New Tun From Scratch](https://www.smarthomebeginner.com/images/2021/09/6-wireguard-android-create-from-scratch-300x636.png)
We are greeted with a new screen.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 13 Blank Tunnel](https://www.smarthomebeginner.com/images/2021/09/6-wireguard-android-new-empty-tun-300x450.png)
Add Known Information
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 14 Interface Section Filled](https://www.smarthomebeginner.com/images/2021/09/7-wireguard-android-interface-filled-300x449.png)
- Start by giving our new tunnel a name. I will be using "wireguard".
- The 'Private Key' can either be copied manually if you have already created one on the "server", or we can generate one using the "double-arrows" icon to the right of the box.
- The 'Public Key' will be automatically generated for us, using the Private key from above.
- Addresses is the IP address we wish to assign on the Android device. To simplify and avoid overlapping IP mapping, I generally use the same range as the server and pick an unused address. If following along with my other articles, this could be something like: 10.254.0.2/32
- Listen port can be left blank and let the app assign its own.
- DNS servers is explained below.
- MTU is best left blank (auto).
Moving to the next section, we need to add our server as a "Peer". Click the 'Add Peer' heading at the bottom of the screen.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 15 Peer Section Filled Out](https://www.smarthomebeginner.com/images/2021/09/7-wireguard-android-peer-filled-300x376.png)
- PublicKey is as the name suggests the Public Key from the Wireguard server.
- Pre-shared Key see below.
- Persistent keepalive as stated is optional and generally not recommended as it will cause frequent pings to the server and use more battery. If you are really struggling to hold a connection to the server, you can consider putting in a number here (in seconds).
- Endpoint is the IP address (or domain name) of our server along with the port it is listening on.
- Allowed IPs sets which IP addresses we want routed through our Wireguard tunnel. To start, I will just be using the same set of addresses available to our Wireguard server.
Click the "Save" icon to close the window.
3. Add Client Details to your Wireguard Server
Now that the Android Wireguard client is set, a few details need to be shared with the machine hosting the Wireguard VPN server. The client has to be added as a peer on the server. This has been described in our Linux Wireguard server guide.
At the very least, the server will need your client's Public Key and Address. Once added to the server, we can continue!
4. Activate the Tunnel!
Click the gray toggle switch to the right of the tunnel name and after a second or so you should see the toggle change to blue and a new "key" icon should appear in the upper notification bar.
Test Your Connection
You can test to make sure your connection is working a few different ways. As Android is roughly based on the Linux kernel, we can use the same Terminal command ping. An example of an app that can act as a Terminal is Termux. In this case, since our server is running on IP address 10.254.0.1, we can simply ping the address and look for a response:
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 17 Ping Wireguard Server From Android](https://www.smarthomebeginner.com/images/2021/09/9-wireguard-android-ping-740x449.png)
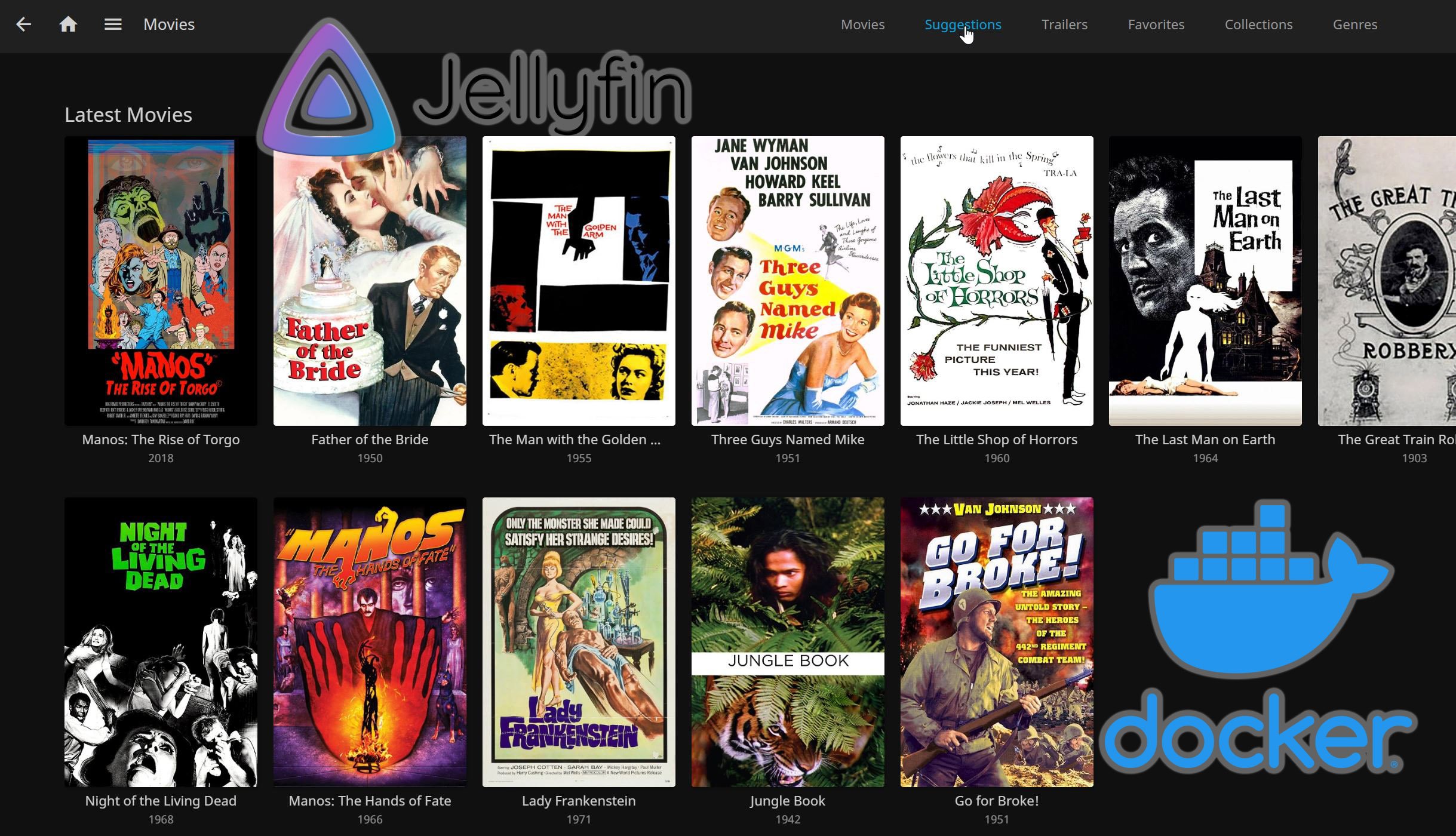
I had also setup a Jellyfin instance on my Wireguard Server to test with, and was easily able to access it using the Wireguard server IP:
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 18 Connect To Jellyfin Via Wireguard](https://www.smarthomebeginner.com/images/2021/09/9-wireguard-android-jellyfin-login-300x304.png)
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 19 Successfully Reach Jellyfin Login Page Via Wireguard](https://www.smarthomebeginner.com/images/2021/09/9-wireguard-android-jellyfin-success-300x490.png)
Be the 1 in 200,000. Help us sustain what we do.Join Us (starting from just $1.67/month)
Access Additional Local Resources
The setup above allows you to connect directly to your Wireguard server and access anything running on it. If you have IP forwarding setup on the server, you can also access other Wireguard peers who are connected to the same Wireguard server.
However, we might have other devices on the local network that the Wireguard server is part of. To connect to those, we simply need to modify our interface just slightly so that the Android device knows to pass requests to those IP's through the Wireguard tunnel (and not directly to the local network you are currently using).
The 'AllowedIPs' Section
Let's say I have an additional device on my home network that isn't attached directly to my Wireguard server; a Raspberry Pi running my Nextcloud server. It is running on our home network with the IP address 192.168.124.109.
Currently, we are at Friend's house, and we type that address into our browser. Our Android device would not be able to find the Nextcloud server. This is because 192.168.124.109 isn't included in the AllowedIPs section of our Wireguard interface. Our browser looks for the device in Friend's network instead of through the Wireguard tunnel to our home network. Let's modify our 'AllowedIPs' to make sure the request is passed through Wireguard:
Edit Our Wireguard Client Adapter Settings
Open your Android Wireguard App and edit the tunnel. Let's add the IP of our Raspberry Pi at home: 192.168.124.109.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 20 Wireguard Android Additional Allowed Ips](https://www.smarthomebeginner.com/images/2021/09/10-wireguard-android-allowedips-300x582.png)
Click the 'Save' icon in the upper right corner. We will see a message at the bottom of the screen saying it was successfully saved.
Head to your browser (or app) and now we type in the 192.168.124.109 address to see if we can reach our Nextcloud.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 21 Successfully Reached Nextcloud Via Wireguard Tun](https://www.smarthomebeginner.com/images/2021/09/10-wireguard-android-nextcloud-success-300x399.png)
Success!
User Defined DNS servers
This section applies to anyone using Pi-Hole/AdGuard Home or who wishes to set custom DNS for their Android device. If you decide not to route ALL of your traffic (described below) through your Wireguard server, you can still add DNS servers to your config. In this example, we add a declaration using Cloudflare's DNS servers.
Open your Android Wireguard VPN App, and edit the tunnel. Add the following in the DNS servers box:
1.1.1.1, 1.0.0.1
Your finished client configuration should look like below:
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 22 Set Wireguard Dns Settings](https://www.smarthomebeginner.com/images/2021/09/11-wireguard-android-DNS-300x388.png)
Click the 'Save' icon and you will see a message at the bottom of the screen confirming the successful configuration change.
I wasn't able to verify via Termux that the new DNS servers were in fact the ones being used due to a 'feature' of Termux. Termux by default uses Google's DNS servers regardless of the device's settings, leading you to believe it didn't work properly. So digging around the internet for a few minutes showed me an app that can help called Network Info II.
Another easy way to verify is by using a DNS leak testing site like https://dnsleaktest.com.
Route All Traffic Through Wireguard Server
Routing all traffic through our Wireguard server is generally quite easy to accomplish from the Android Wireguard App. Open your Android Wireguard App, and edit the tunnel. Next we change AllowedIPs to 0.0.0.0/0.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 23 Set Allowedips To 0.0.0.0/0](https://www.smarthomebeginner.com/images/2021/09/12-wireguard-android-all-traffic-300x590.png)
Excluding Private IP Ranges
At the bottom of the window you might notice there's an additional checkbox that did not exist before we typed in 0.0.0.0/0 - "Exclude private IPs". This setting allows you to pass all of your traffic through your Wireguard VPN EXCLUDING private addresses like 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16.
Be the 1 in 200,000. Help us sustain what we do.Join Us (starting from just $1.67/month)
FAQs
Why can't I connect to another device?
Ensure the device you are trying to connect to is within your 'AllowedIPs' range. Remember that you can set individual IP's or a whole set of IP's. Most home routers use DHCP (dynamic host configuration protocol) which means that a device's IP can change occasionally (especially on router restarts). In this case, you can give a range such as 192.168.1.0/24 to cover all devices in the 192.168.1.1 - 192.168.1.254 range. Also, check your firewall rules.
Can I have more than one Wireguard tunnel active at a time?
Some digging into the Wireguard Android code repository makes it look like it should be possible. However, it might not be available to non-rooted devices. No matter my settings, I was unable to get it to work (using the F-Droid version).
If your device is rooted you might be able to run multiple simultaneous tunnels as long as the address ranges do not overlap.
If rooted, using the Termux app, you can install the wireguard-tools package which will give you access to the wg-quick command. This should work the same as it does in the Linux clients and allow you to bring 'up' as many tunnels as you like.
While not strictly necessary, the Preshared Key adds a layer of security to better protect our tunnel against attacks by advanced threats. Again, not strictly necessary but easy to add in my opinion. The generated key will need to be included in both the server's config file and in your Wireguard Android App.
If your Preshared Key was generated from the server, securely copy it to your Android device. Open your Android Wireguard App, and edit the tunnel. We will add it in the 'Pre-shared key' box under the Peer section.
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 24 Add Psk To Android Wireguard](https://www.smarthomebeginner.com/images/2021/09/13-wireguard-android-psk-300x582.png)
To generate one from your Android you must use the CLI version of Wireguard. To use the CLI, you must install the wireguard-tools package. I installed it using Termux (as linked above) and installed the package with:
pkg install wireguard-tools
This next part follows the Wireguard Linux article, so I will not go in depth. The short version is to use your terminal to generate a Preshared Key (PSK), copy it into both your Android Wireguard App (shown above), and into the server config.
wg genpsk
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 25 Generate Psk On Android](https://www.smarthomebeginner.com/images/2021/09/13-wireguard-android-genpsk-740x184.png)
Can I use Wireguard for Android with IPv6?
Absolutely. Anywhere you see an IPv4 address, you can add a valid IPv6 address as well. Make sure your server can handle IPv6 requests or you might have trouble with the Wireguard tunnel.
How do I export my config if I generated it myself?
In your Android Wireguard App homesecreen, click the three-vertical-dot menu button in the top right corner. Select "Export tunnels to zip file". By default, the .zip file will go to your "Downloads" folder. Be careful what you do with that file, and don't share it with anyone.
Why can't I connect to the Internet after starting my Wireguard tunnel?
As the joke goes... "It's Always DNS". If using 0.0.0.0/0, double check your server is able to resolve domain names (server is connected to the internet). Double check to see if your config settings were entered properly (like mixing keys). Try setting a DNS server as stated earlier in this article. You can also set it to the IP of the server itself if you have something like unbound running.
How do I Include/Exclude an app from using the Wireguard tunnel?
Open your Android Wireguard App, and edit the tunnel. Click on the "All Applications" button at the bottom of the Interface frame. Here you can select to allow/exclude certain apps from using the tunnel.
How can I automatically disconnect the tunnel when I am home, and automatically connect when I leave?
The Wireguard Android App doesn't have this feature natively included (as of this writing). I haven't tried it myself, but a common recommendation is using the Tasker App to automate actions based upon triggers (like joining/leaving a specific WiFi SSID).
Concluding Thoughts
The Wireguard for Android App is a great compliment to the family of Wireguard applications. I find it to be user friendly, but is lacking a bit if you install it with no other notion of how the Wireguard VPN protocol works.
Either way, I appreciate the simplicity and flexibility it offers while abstracting the more complex aspects of VPN's. Wireguard has simplified the VPN setup process so much most enthusiasts and homelab beginners can now implement it easily.

![Wireguard Android Client Setup [2022] - Simple and Secure VPN 1 Wireguard Android Setup](https://www.smarthomebeginner.com/images/2021/09/wireguard-android-setup-header-740x416.webp)
![Wireguard Android Client Setup [2022] - Simple and Secure VPN 16 Tunnel Activated](https://www.smarthomebeginner.com/images/2021/09/8-wireguard-android-tun-active-740x721.png)